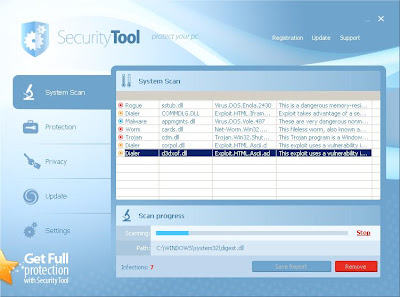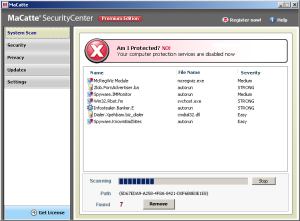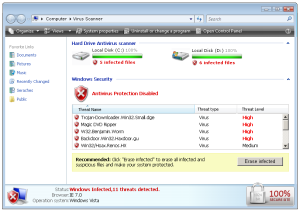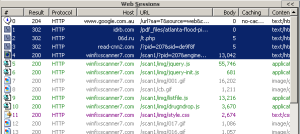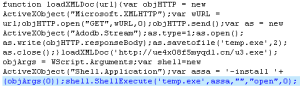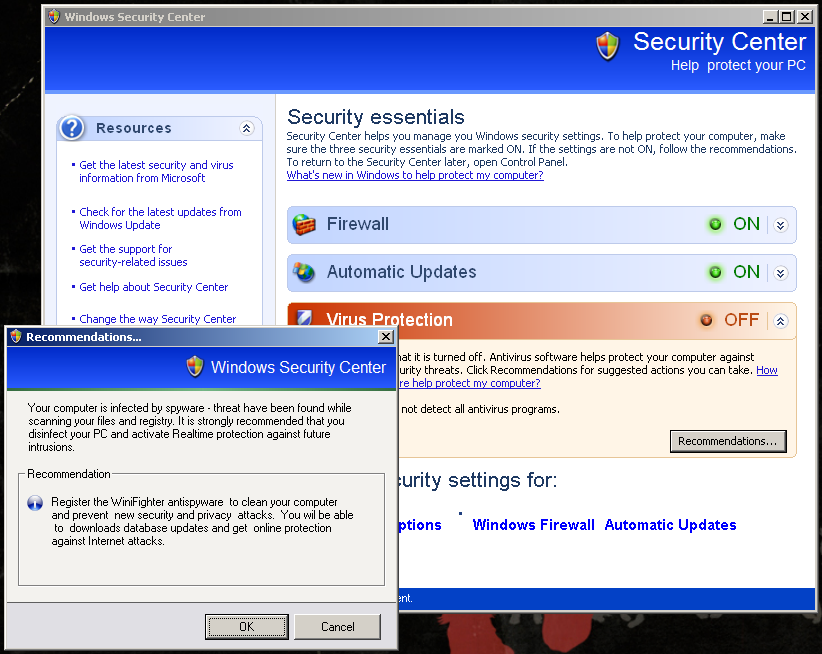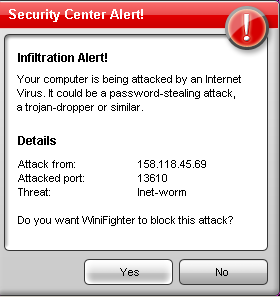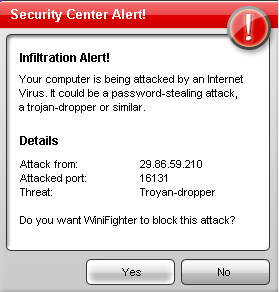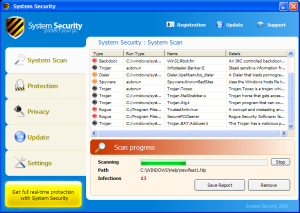
Scareware is BIG business. They use heaps of scare tactics in order to convince unsuspecting users into buying rogue applications. But here's one that does a bit more than just scaring.
System Security terminates almost all running processes. This basically prevents us from using our computers. More importantly, this hinders execution of tools necessary to investigate the infection and aid in removal of this rogue app.
Back in the day, in order to evade detection and removal, malware writers have targeted security-related applications. They have a black list of applications including (but not limited to) the following:
avast.exe
avp.exe
cmd.exe
icesword.exe
kav.exe
regedit.exe
taskmgr.exe
But now they block even the most harmless Windows applications such as calc.exe and notepad.exe. But not all applications should be terminated, because that basically means no Windows. No Windows means no profit so the bad guys need basic Windows functionality. Which tells us that they have probably stopped using blacklisting and shifted to whitelisting instead. They now have a list of applications that they would allow to be executed in the system.
Here's part of some disassembly taken from a sample of System Security, showing us evidence of whitelisting:
Rogue app takes a snapshot of all the processes in the system:
.rsrc:140B4B4F push edi
.rsrc:140B4B50 push 2
.rsrc:140B4B52 call CreateToolhelp32Snapshot
.rsrc:140B4B57 mov [ebp+hObject], eax
...
.rsrc:140B4B79 push ecx
.rsrc:140B4B7A push eax
.rsrc:140B4B7B mov [ebp+var_64C], 22Ch
.rsrc:140B4B85 call Process32FirstW
...
.rsrc:140B4BAB push [ebp+dwProcessId] ; dwProcessId
.rsrc:140B4BB1 push 0 ; bInheritHandle
.rsrc:140B4BB3 push 1FFFFFh ; dwDesiredAccess
.rsrc:140B4BB8 call ds:OpenProcess
It then terminates the processes not found in the white list:
.rsrc:140B4C00 push 0FFFFFFFFh ; uExitCode
.rsrc:140B4C02 push edi ; hProcess
.rsrc:140B4C03 call ebx ; TerminateProcess
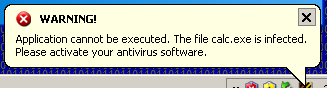
and displays this message as a notification in the system tray:
.rsrc:14039998 aApplicationCan: ; DATA XREF: sub_140B4ADD+16A
.rsrc:14039998 unicode 0,
.rsrc:14039998 unicode 0,
.rsrc:14039998 dw 0Ah
.rsrc:14039998 unicode 0, ,0
.rsrc:14039A5E align 10h
.rsrc:14039A60 aWarning: ; DATA XREF: .rsrc:140104BF
.rsrc:14039A60 ; sub_140B4ADD+1DB ...
.rsrc:14039A60 unicode 0, ,0
.rsrc:14039A72 align 4
It then resumes processing the snapshot created earlier and the cycle continues:
.rsrc:140B4CDF lea eax, [ebp+var_64C]
.rsrc:140B4CE5 push eax
.rsrc:140B4CE6 push [ebp+hObject]
.rsrc:140B4CEC call Process32NextW
Here's the list of applications that the scareware allows:
.rsrc:14046A48 off_14046A48 dd offset aAlg_exe ; DATA XREF: sub_140B49CF+26
.rsrc:14046A48 ; "alg.exe"
.rsrc:14046A4C dd offset aCsrss_exe ; "csrss.exe"
.rsrc:14046A50 dd offset aCtfmon_exe ; "ctfmon.exe"
.rsrc:14046A54 dd offset aExplorer_exe ; "explorer.exe"
.rsrc:14046A58 dd offset aServices_exe ; "services.exe"
.rsrc:14046A5C dd offset aSlsvc_exe ; "slsvc.exe"
.rsrc:14046A60 dd offset aSmss_exe ; "smss.exe"
.rsrc:14046A64 dd offset aSpoolsv_exe ; "spoolsv.exe"
.rsrc:14046A68 dd offset aSvchost_exe ; "svchost.exe"
.rsrc:14046A6C dd offset aSystem ; "system"
.rsrc:14046A70 dd offset aIexplore_exe ; "iexplore.exe"
.rsrc:14046A74 dd offset aLsass_exe ; "lsass.exe"
.rsrc:14046A78 dd offset aLsm_exe ; "lsm.exe"
.rsrc:14046A7C dd offset aNvsvc_exe ; "nvsvc.exe"
.rsrc:14046A80 dd offset aWininit_exe ; "wininit.exe"
.rsrc:14046A84 dd offset aWinlogon_exe ; "winlogon.exe"
.rsrc:14046A88 dd offset aWscntfy_exe ; "wscntfy.exe"
.rsrc:14046A8C dd offset aWuauclt_exe ; "wuauclt.exe"
As we can see, System Security is more than just scareware. You won't be able to properly use your computer unless you buy the rogue app. Sounds more like ransomeware to me.
But, now that we know that it uses whitelisting, we can do a little work around and bypass this technique. We can rename a copy of the tools that we need to run as one of the whitelisted applications and voila! We've already taken one step into regaining full use of our infected computer.