The Hockey games on the 2010 Winter Olympics are well under way and SEO poisoning attacks abound! Hockey enthusiasts turning to the Internet in search of game schedules are in for quite a surprise as cyber-criminals are quick to ensure that their malicious websites appear in the top Google search results.
Redirection
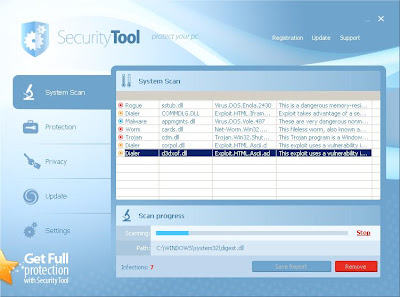
Unsuspecting users who click on the malicious search results are redirected to a fake My Computer online scan page. Here is where the bad guys attempt to 'scare' their way into the user's computers.
Fake My Computer online Scan
Message displaying false detections on the user's computer
Navigating Away
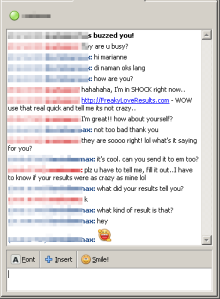
Users attempting to manoeuvre away from the malicious website are presented with the following message and are left with very little choice:
Countermeasure Against the Good Guys Malware researchers often share URLs with each other as a way of spreading the news and to warn others and prevent further infection. But the bad guys behind this attack are smart enough to devise a countermeasure. The URLs are no longer enough to replicate the attack. Entering the URL directly on the browser simply redirects the users to the CNN website.
CNN Website
Download
The fake My Computer online scan page ultimately offers a solution to in the form of an installer of the fake antivirus software called Security Antivirus.
File Download
The Works
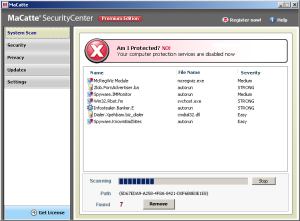
As with other fake security software, Security Antivirus displays a decent graphical user interface to give its victims that warm fuzzy feeling of installing a legitimate software that will protect their computer.
As mentioned in a
previous post, Security Antivirus is a clone of Live PC Care, Windows Security Suite, and Windows System Suite.
Installation
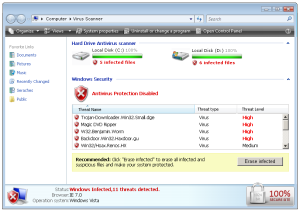
Fake Scans
Annoying Pop ups
As unsuspecting users would like to remove all the purported detections found on their machine, Security Antivirus requires activation. And for a lifetime subscription, victims would have to say goodbye to a hefty $89.95 from their hard-earned cash.
Activation
License Selection
Credit Card Payment
Entering credit card details here seals the deal. But there's no stopping the bad guys from abusing the information they have collected.
If you have been a victim of this attack, immediately contact your credit card company to get your money back and to make sure there will be no future unauthorised charges.
Also, when searching for information relating to the Winter Olympics, it always a good idea to turn to reputable sources like news networks and of course the official
2010 Winter Olympics website.
 Security Essentials 2010 (SE2010.exe) is a new rogue application which is usually arrives as a file dropped by a Trojan or downloaded from the internet. It employs the same techniques as of Internet Security 2010…then again, said techniques have proven effective before, so why fix what is not broken?
Security Essentials 2010 (SE2010.exe) is a new rogue application which is usually arrives as a file dropped by a Trojan or downloaded from the internet. It employs the same techniques as of Internet Security 2010…then again, said techniques have proven effective before, so why fix what is not broken?