Another hot topic circulating around the internet is the Winter Olympics and the hits around the search engines come soaring when the news of the death of a 21 year old luger Nodar Kumaritashvili breaks out. Malware writers are quick on taking advantage of this news to infect computer users browsing every website wanting to be updated. They also use as well as the current medal count at the said Olympics.
Moreoever, the (malware) samples that are found in the previous hot events (such as Haiti Earthquake, Twilight and Superbowl) were all the same kind of Rogue AV found now. They are of the same family, same setup and the same characteristics. It seems that they’re doing this fashion in an automated way. They’re trying to link these hot keywords so that search engines would point the users to their malicious websites where the malware is hosted.
OLYMPIC LUGER’S DEATH
Death of a luger in winter Olympics triggered the Rogue AV writers to use this as a vector of their infection most especially when the actual video of his death is released.

Search result for luger’s death. Clicking the search result (in red box) would redirect to RogueAV
Internet users who wanted to be updated with this news will unknowingly visit one of these malicious sites. Redirections will occur until the user will experience fake AV pop-ups and enticing them to download the malicious installer file..
WINTER OLYMPIC’S MEDAL STANDING
Another Malware Writers takes advantage of as the winter Olympics are on-going is the medal standings of each participating countries. They use keyword such as “Medal Count”, “Olympic medal count”, “Olympic standing” in order to be included in search engines and be able to infect users.
Search result for Winter Olympic Medal Standings. Clicking the search result (in red box) would redirect to RogueAV.

Unaware users who wanted to look for medal standings will unknowingly visit one of these malicious sites. Visiting these malicious URLS will download Rogue AV and make the user’s computer have annoying pop ups.
REDIRECTIONS
Upon clicking the enticing malicious URL / link, there will be redirections and some different enticing pop-up messages or web page for the user to click on it and download a malicious file.
Pop-up messages telling that the user's machine is currently infected:

The URLs used with these redirections are constantly changed to ensure that propagation of this Rogue AVs are always obtainable for every malicious search result and make certain that it will not be blocked by legit Antivirus Vendors.
Download
As of this writing, there were two types of Rogue AV that can infect user’s computer. One is Security Antivirus and the other is Security Tool (which is a constant download even with the previous RogueAVs’ SEO campaign).
- Security Antivirus file to be downloaded:
- packupdate_build<1-3>_<1-3>.exe
- Security Tool file to be downloaded:
- install.exe or player_update.exe
Execution
Security Antivirus
It comes as perfectly legit looking antivirus software enticing the user to download and purchase it. Looking further, we can say that it is a clone or a family of Rogue AVs called Live PC Care, Windows Security Suite, and Windows System Suite. Upon execution of the downloaded sample, installation on computer takes place. It will display a welcome message before installation and then runs in the background making annoying pop-ups. It also tries to stop execution of all legit AV executables through registry modification.
Installation
Main Window
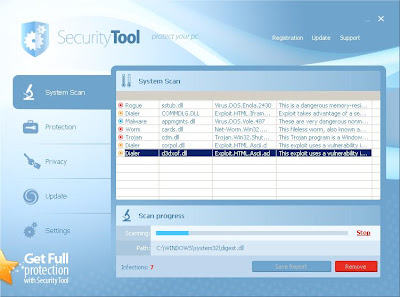
Security Tool
Upon execution of the downloaded sample, installation on computer takes place. It will then silently drop a copy of itself with randomised filename and registry autorun key for automatic execution upon boot up. The user will only know that installation takes place when a message box appears saying that Security Tool successfully installed.
Same with other RogueAVs it will silently run in the background and make annoying fake AV messages. It also has the ability to prevent legit files to be executed when the user tries to.







No comments:
Post a Comment